Difference between revisions of "Transmission Module"
| Line 1,128: | Line 1,128: | ||
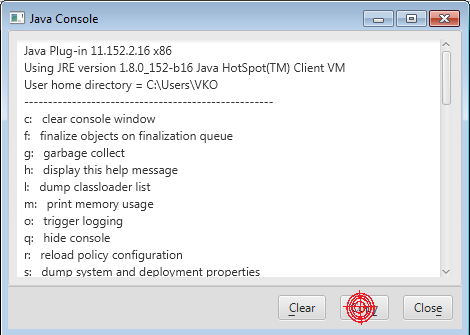
The console will be launched at the first Java call and display all application logs. | The console will be launched at the first Java call and display all application logs. | ||
[[Image:ExJavaConsole.png]] | |||
'''<u>Note</u>: We invite you to send us these logs as plain text copied / pasted into an e-mail'''. | '''<u>Note</u>: We invite you to send us these logs as plain text copied / pasted into an e-mail'''. | ||
Revision as of 13:00, 22 May 2018
Operating mode
The Transmission Module is a Java application automatically launched through JavaWebStart by clicking a web page hyperlink.
JavaWebStart can also manage the automatic update if a new version of the module is available on the server.
Main functionalities of the Transmission Module:
- Encryption and decryption of documents
- Transmission of documents to supervisory authorities
- Keystore generation
- Certificate Request generation and activation
System requirements
e-file is compatible with all Windows and Mac Os versions.
The only real requirement, in addition to internet access, is to have a 1.7 or above execution environment
This can be downloaded directly from Java official webpage, and following the default installation link.
Reporting services using www.e-file.lu
| Additional information | |
|---|---|
| Java Runtime Environment (JRE) | At least Java version 1.7 or above needs to be installed on each computer that needs to encrypt or decrypt data. |
| Java web start enabled | The Transmission Module is launched using Java Web Start which is part of the default installation of a JRE. |
| Java settings | General and Security level settings within the Java Control Panel |
| Proxy, antivirus | Your system (proxy, antivirus,...) must allow .jar and .jnlp files to be downloaded The ports 80 (HTTP) and 443 (HTTPS) must be enabled as well as those URLs : www.e-file.lu/WSEfileFlex, www.e-file.lu/WSEfile, www.e-file.lu/ECH |
| Read and write access to e-file working folders | The Transmission Module needs read and write access to e-file working folders. Therefore, the keystore is imported by default in the "workdir" directory on the C:\ drive: C:\Users\<username> \efile\workdir. |
| Adobe Flash Player | Adobe Flash Player 10.2.0 or above has to be installed on your computer. |
| Cookies | Cookies have to be enabled How to enable Cookies |
| Web browsers | e-file is compliant with most current browsers. Please call us if you have a particular configuration. |
| Chrome |
The default installation of Chrome works correctly. |
Internet Explorer  |
(-) At least Internet Explorer version 11 needs to be installed on your computer.
(-) 'Do not save encrypted pages to disk' has to be unchecked. Warning (only e-file version 1, previous e-file portal): Particular case for IE8. |
Firefox 
|
The default installation of Firefox works correctly Please refer to the section : Firefox and Safari compatibility. |
Safari 
|
The default installation of Safari works correctly Please refer to the section : Firefox and Safari compatibility.
|
Luxtrust certificate
| Additional information | |
|---|---|
| LuxTrust certificate order | For encryption purposes, a Luxtrust SSL certificate is mandatory to use our services. To be able to order the certificate on Luxtrust’s webpage www.easyssl.lu you need to use a modern browser (Chrome, Firefox, Safari, IE10 ...) |
LUXTRUST certificate purchase order
All reporting files transmitted to the supervisory authorities must be encrypted.
The only certificates authorised for the file encryption by the reporting entity are SSL certificates from the certification authority LUXTRUST.
Key and Certificate Request generation
Please be informed that during the next steps two files will be generated:
- the keystore file keystore.ks containing your new keys
- the certificate request file Certificate Request.txt containing a copy of your new keys. This file will be renamed to Certificate Request.csr and uploaded on LUXTRUST´s website during your purchase order. =>Chapter 3.2 Finalize your purchase order of LUXTRUST e-file SSL certificate
Step 1
Important note : the Luxtrust SSL certificate purchase order and its activation have to be performed on the same computer workstation.
Step 2
Connect to e-file v1 with your e-file administrator credentials (adminXXX)
Step 3
Click the link Certificate activation
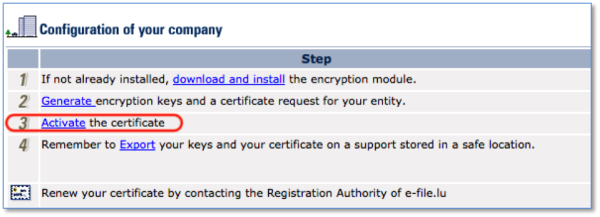
Step 4
Click the link Generate encryption keys and a certificate request for your entity
Step 5
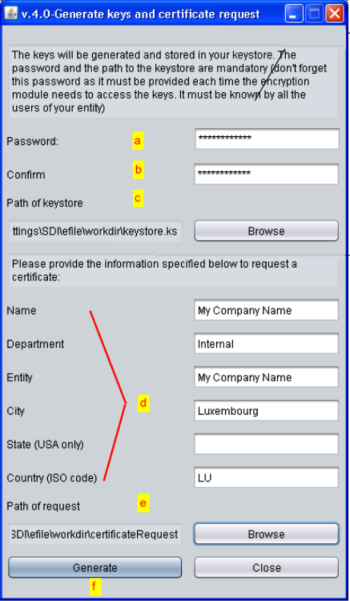
The form Generate keys and certificate request opens :
Step 6
Complete the form
a. Password
If you order the certificate for the very first time, you have to define a brand-new keystore password.
Important note : the keystore password has to be shared with all e-file users who have to transmit encrypted documents or decrypt feedback files received from the supervisory authorities. .
Important note : if you loose your keystore password, you will have to generate a new key and order a new certificate.
In the case you have to renew your certificate, e.g. its validity date expired, you have to use the keystore password that had been created when you ordered the certificate for the very first time.
b. Confirm
Confirm the password
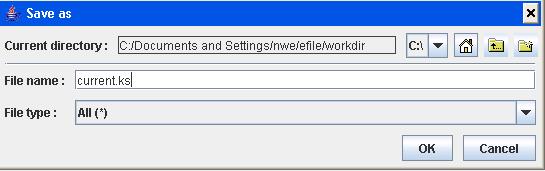
c. Path of keystore
Click the Browse button. A Save As dialog box opens. Complete the required information:
-Current directory:
If you order the certificate for the very first time, select the folder where the keystore file will be stored.
Important note : please ensure that you have write access to this folder .
We suggest using your personal folder: C:\Users\xxx\efile\workdir.
In the case you have to renew your certificate, you have to select your current and valid keystore.ks. Normally, the system remembers the path where it had been stored.
- File name: choose your keystore name, for example keystore.ks
- File type : .ks
d. Name, Department, Entity, City, State (USA only) , Country (ISO code) should be completed as indicated in the above print screen.
e. Path of request
Click the Browse button. A Save As dialog box opens. Complete the required information:
- Current directory: select the folder where the Certificate Request file will be stored.
Important note : please ensure that you have write access to this folder .
We suggest using your personal folder: C:\Users\xxx\efile\workdir
- File name: CertificateRequest.txt
- File type : .txt
f. Generate
Click the Generate button. A window will pop up and confirm that two files have been generated: keystore.ks and CertificateRequest.txt on e.g. C:\Users\xxx\efile\workdir.
Important note : if you renew your certificate, please ensure that the modification date of your current kestore.ks has been updated. If it is not the case it is highly probable that Java has no write access to the folder where the keystore.ks is located
Important note : we advise you to back up the keystore.ks and CertificateRequest files.
Step 7
LUXTRUST´s website where the Certificate Request file will be uploaded, only allows .csr file extension. Therefore, you must rename your CertificateRequest.txt as follows CertificateRequest.csr
Finalize your LUXTRUST purchase order
-Open the LUXTRUST easy SSL e-file website.
-Choose the period of validity of your certificate (1 or 3 years) and click the ORDER E-FILE button.
-If you do not have a LUXTRUST easy SSL e-file account you have to get registered.
-Once registered, complete the whole order form and finalize your purchase order by uploading your CertificateRequest.crs file, accepting the TERMS AND CONDITIONS and clicking the PLACE ORDER button.
-Shortly afterwards, you will receive an e-mail from LUXTRUST confirming your purchase order.
-Please follow all instructions provided in the e-mail and its PDF attachment (Send signed PDF by post with all required documents to the address indicated inside, process the payment etc.)
Activation of your LUXTRUST certificate
The certificate file will be sent to the e-mail address you provided in your purchase order.
The extension of this file will be .txt, in order to prevent your firewall from blocking the attached file.
Step 1
Important note: save the file .txt on your computer workstation and replace the .txt extension by .cer
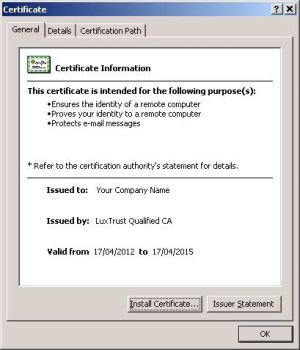
Open the .cer file. You should be able to see your certificate as shown below:
Step 2
Important note : the Luxtrust SSL certificate ordering and its activation have to be performed on the same computer workstation.
Connect to e-file v1 with your e-file administrator credentials (adminXXX)
Step 3
Click the Certificate activation link
Step 4
Click the Activate the certificate link.
Step 5
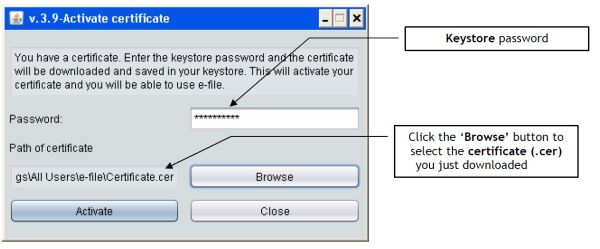
A dialogue box Activate certificate opens
Step 6
Complete the required information
Password
Enter your keystore password
Path of certificate
Select your certificate file (.cer)
Activate
Click the Activate button.
A window will pop up and inform you that the activation has been done successfully.
Your keystore.ks is now activated. It contains your LUXTRUST certificate and your encryption keys.
Important note : we advise you to back up the activated keystore.ks and its password
Important note : if you loose your keystore and/or its password,you will have to generate a new encryption key and order a new certificate. .
Deploying the keystore
The activated keystore, containing your LUXTRUST certificate and your encryption keys must now be provided to the workstations of each e-file user.
=> Installing a new e-file workstation e-file v1 and e-file v2
Sending Service
In the case you are using the Sending Service for your automatic reporting transmission, the activated keystore.ks must be provided as well.
Registration of your certificate with the CSSF
For some reportings, the LUXTRUST e-file SSL certificate used by the reporting entity must be registered with the CSSF, before sending any files, according to the registration procedure described in the CSSF 08/334.
The LUXTRUST e-file SSL certificate must be registered with the CSSF for the below reportings:
- FINREP (CSSF circular 08/344)
- COFREP (CSSF circular 08/344)
- ESP (Special enquiries; CIRCULAR CSSF 08/344)
- PFS reporting (Other professionals of the financial sector; CIRCULAR CSSF 08/369)
- SICAR (Sociétés d´investissement en capital à risque)
- Bank Reporting (CIRCULAR CSSF 10/457; CIRCULAR CSSF 15/624)
- Management companies (CIRCULAR CSSF 10/467)
- Payment institutions (CIRCULAR CSSF 11/511)
- Electronic money institutions (CIRCULAR CSSF 11/522)
- OTHER reporting
- AIFMD reporting (CIRCULAR CSSF 14/581)
=> e-file User Guide: CSSF Certificate registration - General
=> e-file User Guide: CSSF Certificate registration - AIFMD
Installing a new e-file workstation
Installing a new e-file workstation is quick and easy
Installation of e-file v1 workstation
Connect to e-file v1 with your user credentials.
Click the link Configure my workstation security settings.
Click the Configure my workstation security link at the top right of home page, then on Import link (Point 2 in new window)
Enter your keystore Password (password you use each time you send encrypted files via the Transmission Module) 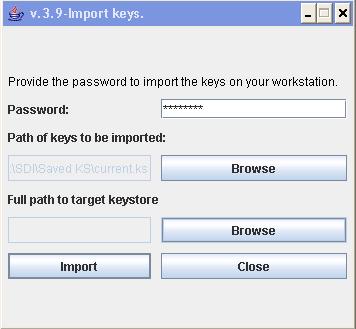
Click the first Browse button and select the valid keystore file (.ks) of your company (Path of keys to be imported)
Click the second Browse button and select the drive and folder where the keystore will be stored (Full path to target keystore).
Please ensure that you have write access to this folder. By default, we suggest to use your personal folders ex: C:\users\xxx\efile\workdir.
Once the folder selected, you have to enter the File name of your destination keystore file. We strongly advise you to use the same name you used for the source file.
Click the 'Import' button.
A window will pop up and confirm that the keystore.ks has been imported.
Installation of e-file v2 workstation
The Transmission Module has to be configured when it is used for the first time (or after each Java update).
Connect to e-file v2 with your user credentials.
The path to the keystore has to be selected with the ![]() button and the key (locally or on a server) will have to be imported with the
button and the key (locally or on a server) will have to be imported with the ![]() button :
button :
Once the keystore.ks has been imported, the access to the keystore is memorized by the application.
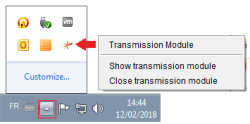
In order to be more user friendly and to speed up the sending process, the Transmission Module will then run as a background process on your desktop.
If you need to end the process, right click on the icon in the taskbar and select “CloseTransmission Module” :
Alert notifications
Please be informed that you can receive alert notifications by email triggered by specific events.
Example : Court orders sent by the Luxembourgish judicial police (=> CSSF - Circular 13/566)
If you want to be notified by email each time the Luxembourgish judicial police sends you court orders, you have to follow the steps below.
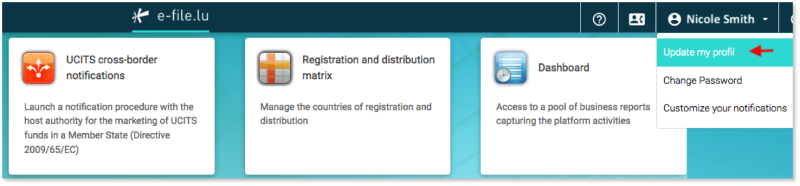
Step 1 : Connect to e-file with your user credentials : https://www.e-file.lu/e-file/
Step 2 : Select Update my profile
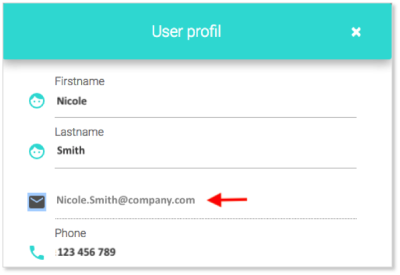
Step 3 : Verify that your email address registered in your e-file account is valid.
IMPORTANT : if your email address is not valid, please ask your e-file administrator to replace it by a valid one.
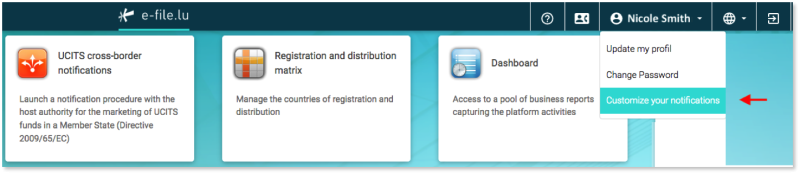
Step 4 : Select Customize your notifications.
Step 5 : Select group « Perquisitions électroniques – Manager ».
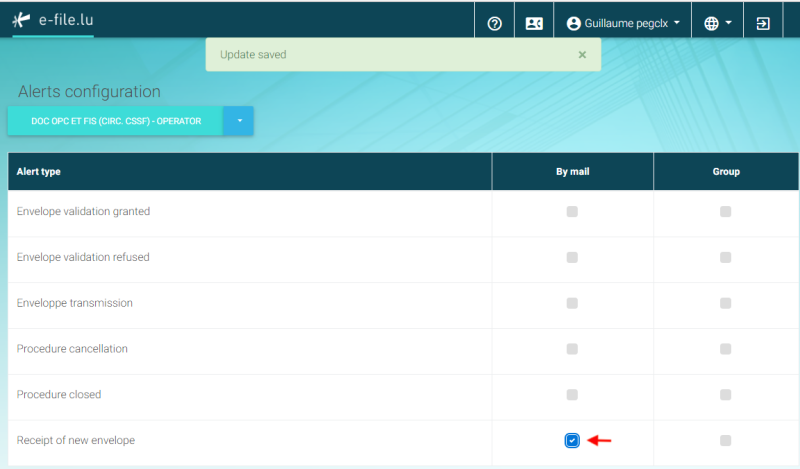
Step 6 : Select « Receipt of new envelope ».
IMPORTANT :
A green window will pop-up stating that the update has been saved.
Manual file transmission
Our Transmission Module allows you to submit reports and documents to Luxembourg authorities.
How to access the Transmission Module
Step 1: Select your environment
Production environment : https://www.e-file.lu/e-file/
Homologation environment (Test) : https://homologation.e-file.lu/e-file/
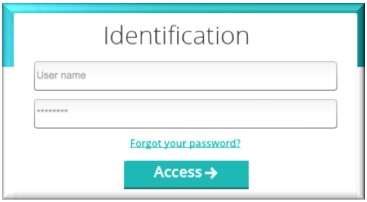
Step 2: Enter your e-file login credentials (user name and password) and click the Access button
Important: If you do not have an e-file user account or if you do not remember your password, you might contact your e-file administrator of your company.
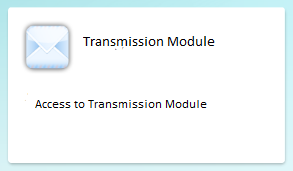
Step 3: Double-click the Transmission Module icon:
Result: the EfileCrypto.jnlp file is generated
Important: the .jnlp file has to be downloaded locally on your computer and must be opened to launch the Transmission Module.
Note: the Transmission Module is a Java application. The Transmission module aims at encrypting documents before they are sent to authorithies. It is also used to decrypt documents and feedbacks.
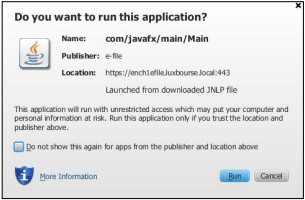
Step 4: Click the Open button of the EfileCrypto.jnlp file
Result: the window below opens
Step 5: Click thebutton
Result: the Transmission Module is launched
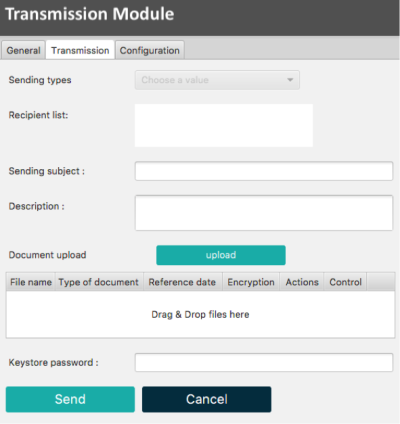
Transmission tab
The Transmission tab has to be used if your file / document is ready to be submitted to the supervisory authority.
How to submit documents/reports to regulators
-Select the Transmission tab of the Transmission Module -Select the Sending type -Enter the Sending subject -Enter the Description -Click the Upload button and upload your file or drag & drop your file in the middle of the window (=>drag & drop files here) -Enter your Keystore password -Check if all fields are completed -If the Control light becomes green you can click the Send button
Special case: UCI attestation request
-Select the Transmission tab of the Transmission Module -Select the Sending type: CSSF attestation -Enter the Sending subject -Enter the Description -No file has to be attached -Enter your Keystore password -Check if all fields are completed -If the Control light becomes green you can click the Send button
Sending types
| Sending type | Reporting | Example | Detailed information | Internal technical business ID |
|---|---|---|---|---|
| Mifir reporting | TAFREP | TAFREP-B00000001-2017-04-15-123456.xml | CSSF - TAF Handbook | bus 71 wkf 111 |
| AnaCredit | ANTREF ANTT1M ANTT2M ANTT2Q |
ANTREF_201801_LUB00999_20180205-001.xml ANTT1M_201801_LUB00999_LUB00999_20180205-001.xml ANTT2M_201801_LUB00999_LUB00999_20180205-001.xml ANTT2Q_201803_LUB00999_LUB00999_20180405-001.xml |
BCL - Reporting instructions | bus 74 wkf 122 |
| FINREP report | B2.4 B2.5 |
FRCREP-B9999-2007-12-B24-L2-L-N--B24.XML FRCREP-B9999-2007-12-B24-L2-L-N--.zip |
Naming convention for CSSF reportings | bus 73 wkf 86 |
| Reporting EDIFACT | B4.4 (Credit institutions) | B0001809.T01 | (-) CSSF - Reporting instructions Edifact B4.4 (-) Naming convention for CSSF reportings |
bus 73 wkf 86 |
| COREP report | COFREP | COFREP-B00000999-2014-03-CCOREP-00-L-N-S-CCOREP.xbrl COFREP-B00000999-2014-03-CCOREP-00-L-N-S.zip |
(-) CSSF - Reporting requirements for credit institutions (-) Naming convention for CSSF reportings |
bus 72 wkf 85 |
| Credit institution reporting | AR: Annual Report CO: Compliance Report GR: Governance Report IA: Internal Audit Report IC: ICAAP LF: Long Form Report ML:ManagementLetter RC: Risk Control Report RP: Recovery Plan SC: Single Customer View |
DOCREP-B00000998-00000000-0000-2009-12-31-AR-DE-0000.pdf |
(-) CSSF - Circular 15/624 |
bus 27 wkf 92 |
| BCL statistics | S0.1; S1.1; S1.4; S1.5; S1.8; S1.9; S2.5-L; S2.5-N; S2.8; S2.9-L; S 2.9-N; S3.2 |
S0001_L1_20130616_B000000999_B000000999_20130617_001.xml | (-) BCL - Manual of electronic transmission for statistical reports of banks | bus 13 wkf 96 |
| Security by security Banks | TPTBBL; TPTBBN; TPTBHR; TPTBHN | TPTBBL_L4_201804_B000000999_B000000999_20180617_001.xml | (-) BCL - Manual of electronic transmission for statistical reports of banks | bus 20 wkf 97 |
| Payments balance | BOP | BOP101_20130616_B000000999_B000000999_20130617_001.xml | (-) BCL - Manual of electronic transmission for statistical reports of banks | bus 12 wkf 105 |
| CSSF enquiry | ESPREP | ESPREP-B0999-2008-06-STT.xls | (-) Naming convention for CSSF reportings | bus 15 wkf 78 |
| EDP report | EDPREP | EDPREP-Z9999-2011-03-Z11-L0-L-N--.xls | (-) CSSF - Reporting instructions |
bus 29 wkf 109 |
| EME report | EMEREP | EMEREP-W9999-2011-03-W11-L0-L-N--.xls | (-) CSSF - Reporting instructions (-) Naming convention for CSSF reportings |
bus 34 wkf 110 |
| Data payment collection (CDP) | V1.1 - V1.14 | V0101_L2_201601_W000000003_B000000999_20160201_001.xml | BCL - File name convention | bus 36 wkf 74 |
| Reporting U | U1.1 | U11REP-B00000012-O00008450-00000002-201512-RAP-1421893257541.xml | (-) CSSF - Circular 15/627 |
bus 8 wkf |
| Reporting Sicar | SICREP | SICREP-B999999-K999990000-2008-06-K31-L0-L-N.xls |
(-) CSSF - Circular 08/376 |
bus 17 wkf 112 |
| Management letters CSSF 09/423 | Management letters (ML) =>PDRREP Other auditor report (RR) =>DOCREP |
PDRREP-O000001234-2018-01-15-ML.pdf DOCREP-O00001234-00000014-0001-2018-01-15-RO-EN-0000.pdf |
(-) CSSF 09/423 |
bus 21 wkf 82 |
| Long forms CSSF 09/423 | Long Form reports (LF) =>PDRREP Other auditor report (RR) =>DOCREP |
PDRREP-O000001234-2018-01-15-LF.pdf DOCREP-O00001234-00000014-0001-2018-01-15-RO-EN-0000.pdf |
(-) CSSF 09/423 |
bus 21 wkf 81 |
| 08/371 FIS prospectus | SIF: (-) Prospectus (PC) |
DOCREP-O00001234-00000014-0001-2018-01-15-PC-EN-0000.pdf |
CSSF - Document transmission Circulars 08/371, 09/423, 11/509 |
bus 21 wkf 83 |
| 08/371 UCI prospectus | UCI: (-) Prospectus (PC) (-) Simplified prospectus (PS) (-) Letter of explanation (LE) |
DOCREP-O00004321-00000014-0001-2018-01-15-PC-EN-0000.pdf |
CSSF - Document transmission Circulars 08/371, 09/423, 11/509 |
bus 21 wkf 84 |
| 08/371 FIS report | SIF: (-) Annual Report (AR) (-) Semi-annual report (SR) (-) Letter of explanation (LE) (-) Other periodic report (RO) (-) Movements in the securities portfolios (PM) |
DOCREP-O00001234-00000014-0001-2018-01-15-ARR-EN-0000.pdf |
CSSF - Document transmission Circulars 08/371, 09/423, 11/509 |
bus 21 wkf 87 |
| 08/371 report | UCI: (-) Annual Report (AR) (-) Semi-annual report (SR) (-) Letter of explanation (LE) (-) Other periodic report (RO) (-) Movements in the securities portfolios (MP) |
DOCREP-O00004321-00000014-0001-2018-01-15-AR-EN-0000.pdf |
CSSF - Document transmission Circulars 08/371, 09/423, 11/509 |
bus 21 wkf 89 |
| Management regulation/status | (-) DOCREP MR: Management Regulations of UCITS (MR) (-) DOCREP AI: Articles of Incorporation of UCITS (AI) |
DOCREP-O00004321-00000014-0001-2018-01-15-MR-EN-0000.pdf |
CSSF - Document transmission Circulars 08/371, 09/423, 11/509 |
bus 21 wkf 108 |
| Key investor document | Key Investor Information Document | DDOCREP-O00009876-00000004-0008-2018-01-15-KI-EN-0000.pdf | (-) CSSF 11/509 (-) CSSF - Document transmission Circulars 08/371, 09/423, 11/509 |
bus 21 wkf 106 |
| CSSF attestation | CSSF attestation request | - | - | bus 21 wkf 104 |
| AIF Reporting | AIFREP | AIFREP-P12345678-A00000001-F00000000-000000000-MAN-20140129145000.zip AIFREP-P12345678-A00000111-V00002222-00003333-AIF-20140129145000.zip |
CSSF - Circular 14/581 | bus 54 wkf 24 |
| Management company report | SGOREP | SGOREP-S9999-2009-03-G21-L2-S-N--.xls |
(-) CSSF - Circular 10/467 |
bus 26 wkf 95 |
| PSF report | PSFREP | PSFREP-P9999-2008-03-P11-L1-L-N--.xls |
(-) CSSF - Circular 05/178 |
bus 18 wkf 94 |
| Titrisation vehicles | S2.14 S2.15 TPTTBS |
S0214_L1_201412_T000000999_T000123001_20150120_001.xml S0215_L1_201412_T000000999_T000123001_20150120_001.xml TPTTBS_L1_201412_T000000999_T000123001_20150120_001.xml |
(-) Circular 2014/236 |
bus 23 wkf 98 |
| Issuing companies reporting | S2.16 S2.17 |
S0216_L1_201406_DSE0003524_DSE0003524_20140720_001.xml S0217_L1_201406_DSE0003524_DSE0003524_20140720_001.xml |
(-) BCL - Reporting instructions S2.16, S2.17, TPTIBS | bus 35 wkf 90 |
| Reporting securities by securities of issuing companies | TPTIBS | TPTIBS_L1_201406_DSE0003524_DSE0003524_20140720_001.xml | (-) BCL - Reporting instructions S2.16, S2.17, TPTIBS | bus 35 wkf 90 |
| Rapport narratif (CAA) (Companie) - Governance Re |
VN01; N02; N03; N04; N07; N08; N09; N10 no source files |
N01V-LU-01-20160331-CAA-LEIDéclarant-LEIDéposant.xbrl | (-) Circulaire 15/10 (-) File naming convention |
bus 62 wkf 64 |
| Rapport narratif (CAA) (Réviseur) - Governance Rep |
N05; N06 no source files |
N05V-LU-01-20160331-CAA-LEIDéclarant-LEIDéposant.xbrl | (-) Circulaire 15/10 (-) File naming convention |
bus 62 wkf 63 |
| Solvency II Reporting | XBRL Solvency II reports no source files |
S01V-LU-01-20160331-CAA-LEIDéclarant-LEIDéposant.xbrl | (-) Circulaire 15/10 (-) File naming convention |
bus 62 wkf 44 |
| FATCA sending | FATCA | FATCA_20150520080022_F0_2016_B_1970010112345_006M8M.00000.LE.442_P.xml | bus 60 wkf | |
| CRS report | CRS | CRS_20170615114523_CRS701_2016_B_19751234567_01234567890M00000000_P.xml | (-) ACD-CRS (-) Newsletter 06/02/2017 (-) ECHA-n°4 06/02/2017 |
bus 68 wkf |
| OTHER reporting (=> CSSF) | OTHREP | OTHREP-B9999-HELLO_WORLD.xlsx | Naming convention for CSSF reportings | bus 19 wkf 93 |
| Various correspondence (OTH) | OTXREP | OTXREP-B0nnn-BOP_IDE_2015_B0nnn_20160615_001.xls | BCL Reporting Instructions | bus 22 wkf 93 |
| Non LU UCI registration | KIID, prospectus, FactSheet... | KIIDOC-2017-12-21-EN-LU-2017-12-21-IE0012345678-12121212.pdf | - | bus 30 wkf 107 |
| Divers/Autres | tbd | tbd | - | bus 5 wkf 73 |
| SIAG (03/108) | tbd | tbd | - | bus 5 and 1 wkf 71 |
| Management company end | tbd | tbd | - | bus 5 and 1 wkf 80 |
| Modification société gestion | tbd | tbd | - | bus 5 and 1 wkf 70 |
| Modification group UCI | tbd | tbd | - | bus 5 and 1 wkf 69 |
| Modification UCI | tbd | tbd | - | bus 5 and 1 wkf 68 |
| Agrément société de gestion | tbd | tbd | - | bus 5 and 1 wkf 67 |
| UCI agreement | tbd | tbd | - | bus 5 and 1 wkf 66 |
| 08/371 report not in 08/371 | tbd | tbd | - | bus 5 and 1 wkf 66 |
| Envoi de documents à la CSSF | tbd | tbd | - | bus 1 wkf 79 |
| Notification 2002/77 | tbd | tbd | - | bus 1 wkf 72 |
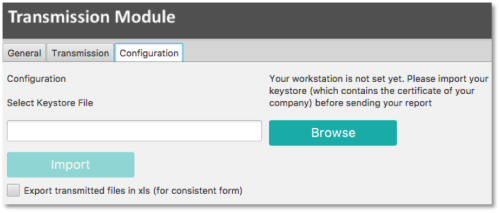
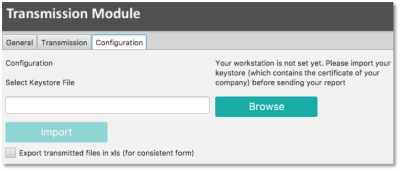
Configuration tab
The Transmission Module has to be configured when it is used for the first time or after each Java update.
The path to the keystore has to be selected with the ![]() button and the key (locally or on a server) has to be imported with the
button and the key (locally or on a server) has to be imported with the ![]() button. The access to the keystore will be automaticaly memorized by the application
button. The access to the keystore will be automaticaly memorized by the application
In order to be more user friendly and to speed up the sending process, the Transmission Module will then run as a background process on your desktop.
If you need to end the process, right click on the icon in the taskbar and select “Close Transmission Module” :
General tab
The General tab has to be used in the following cases:
Case 1:
(-) Transmission of all reportings that have been generated by our Report Generation module and transmitted through the Transmission button available in the form.
=> List of all reportings that can be created manually with our Report generator
Case 2:
(-) Transmission of replies to source files initiated by the supervising authorities
| Report naming convention |
Detail | Supervising authority | Circular | e-file User Guide |
|---|---|---|---|---|
| SPJ | Replies to Notification and execution of court orders 646REP 663REP 664REP |
CSSF | Circular 13/566 | How to reply to court orders issued by investigating judges of Luxembourg |
| U11 | Replies to to U11 (Global Feedback) | CSSF | (-) CSSF - Circular 15/627 (-) CSSF - Circular 12/540 (-) CSSF - File naming convention U1.1 reporting |
How to reply to U1.1 Global feedback |
| CPR, RAC, RDI, RGO,RLB, RRE, ESP, ETR, RSO,FIR |
Replies to source files received from the CAA | CAA | (-) Circulaire 15/10 (-) File naming convention |
Wiki-CAA Manual |
Solving the most common problems
Java settings - Control Panel
(1) Open the Java Control Panel
(-) Launch the Java Control Panel on Windows
-Launch the Windows Start menu
-Click on Programs (All Apps on Windows 10)
-Find the Java program listing
-Click Configure Java to launch the Java Control Panel
(-) Launch the Java Control Panel on Mac (10.7.3 or above)
-Click on Apple icon on upper left of screen
-Go to System Preferences
-Click on the Java icon to access the Java Control Panel
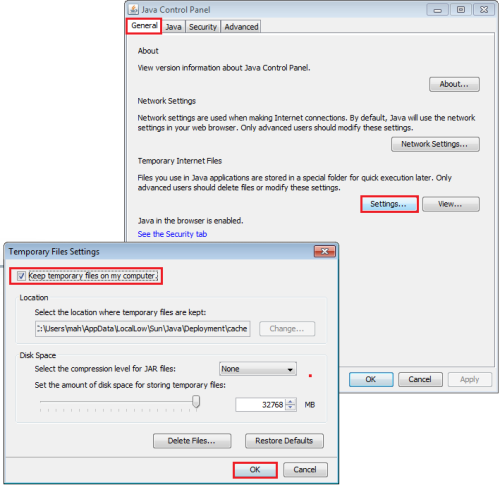
General tab
(2) Configure the Java temporary files settings as indicated on the printscreen below:
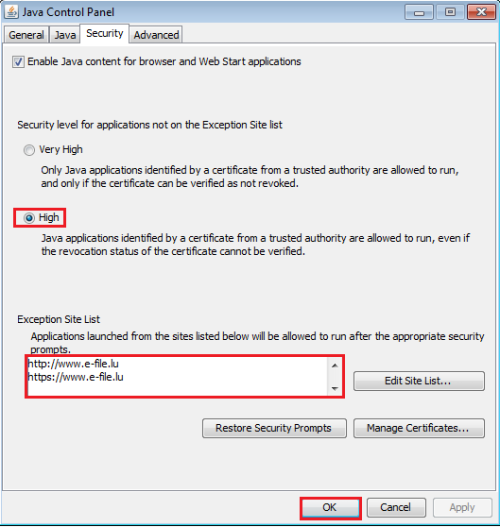
Security tab
(3) Configure the Java security settings as indicated on the printscreen below:
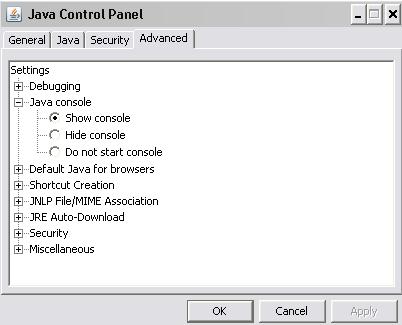
Advanced tab
In case of Java error messages, we strongly recommand to enable your computer's Java Console.
The Java Console provides information about the Java version, user home directory, and any error messages that may occur.
How to enable Java Console in Control Panel:
1. Click Start.
2. Select Settings.
3. Select Control Panel.
4. Double click the Java icon.
5. Click the Advance tab.
6. Click on the + sign
7. Select Show Console and click Apply.
The console will be launched at the first Java call and display all application logs.
Note: We invite you to send us these logs as plain text copied / pasted into an e-mail.
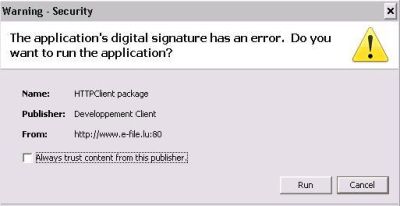
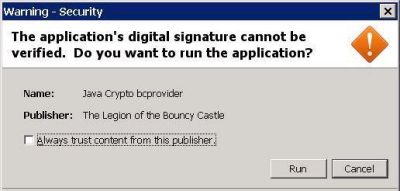
First use warning
The messages below are security warnings which mainly popup during the first use of e-file.
Solution:
Select the checkbox label Always trust content form this publisher to prevent these warnings to appear every time you use the Transmission Module.
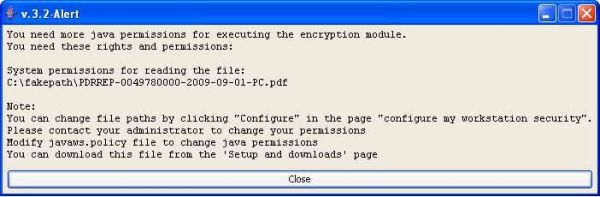
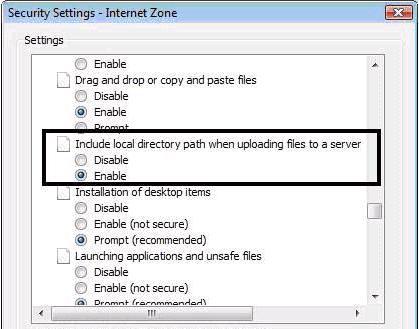
IE 8 Configuration - Fakepath Problem
Version 8 of Internet Explorer do not allow to retrieve the full path of a document when it is selected from the local file system.
You may receive the below Alert:
Solution:
1. In Internet Explorer 8, navigate to Tools > Internet Options.
2. On the Security tab, select a network zone.
3. Click Custom Level.
4. Scroll down to the Include local directory path when uploading files to a server entry.
5. Select Enable.
6. Click OK and click Apply.
Reporter is blocked
The message below is generated if your LUXTRUST e-file SSL certificate has not been registered with the CSSF.
For some reportings, the LUXTRUST e-file SSL certificate used by the reporting entity must be registered with the CSSF, before sending any files, according to the registration procedure described in the CSSF 08/334.
The LUXTRUST e-file SSL certificate registration must be applied to the below reportings:
- FINREP (CSSF circular 08/344)
- COFREP (CSSF circular 08/344)
- ESP (Special enquiries; CIRCULAR CSSF 08/344)
- PFS reporting (Other professionals of the financial sector; CIRCULAR CSSF 08/369)
- SICAR (Sociétés d´investissement en capital à risque)
- Bank Reporting (CIRCULAR CSSF 10/457; CIRCULAR CSSF 15/624)
- Management companies (CIRCULAR CSSF 10/467)
- Payment institutions (CIRCULAR CSSF 11/511)
- Electronic money institutions (CIRCULAR CSSF 11/522)
- AIFMD reporting (CIRCULAR CSSF 14/581)
=> CSSF Certificate registration - General
=> CSSF Certificate registration - AIFMD
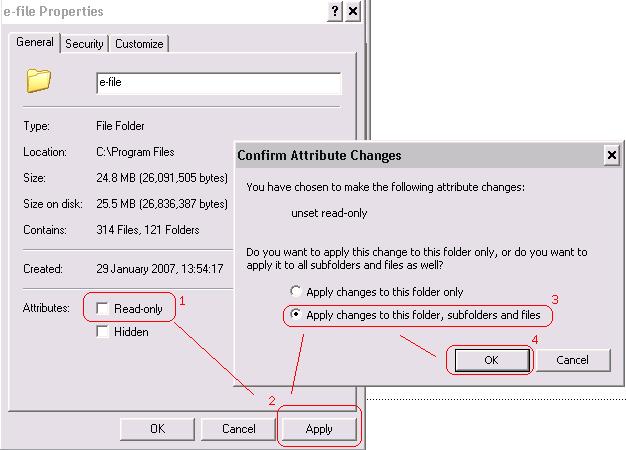
Write rights
The Transmission Module requires read AND write access on the e-file directory in order to run properly.
These error messages reflect access problems.
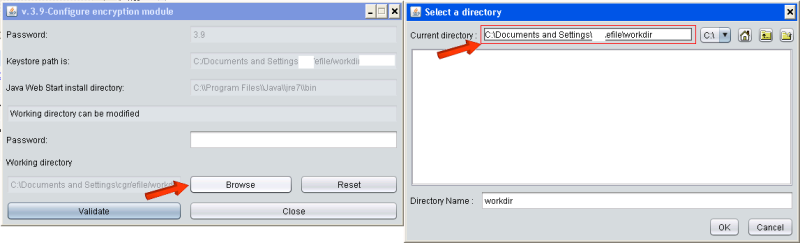
How to retrieve the path of your e-file directory:
1. Connect to e-file v1
2. Click the link Configure my workstation security
3. Click the link Configure the encryption module
4. A Java windows opens, click Browse
5. The path of the e-file directory will be written here :
In order to get read AND write access on the e-file directory, please follow the steps below:
Right click on the e-file directory > properties ... > disable the checkbox label 'Read Only'
If your internal security allows that action, you must also adapt your user rights to all e-file sub-directories.
Note: If you are not allowed to perform such an action, we invite you to contact your IT department so that they can do it for you.
Firefox and Safari compatibility
Like IE8, Firefox version 3 and the Safari browser don't retrieve by default the full path of a document when it is selected from the local file system
Unlike the Microsoft browser, Firefox and Safari do not allow the user to modify the security settings by himself.
We have adapted our application for this particular case by replacing the 'browse' button by a simple text field.
To join a document to an envelope, the user has to copy/paste the whole path of the file in this text field
PC Example : C:\Documents and Settings\xxx\Desktop\[myFile].[myExtension]
MAC Example : /users/[myUser]/Desktop/[myFile].[myExtension]
Running JNLP
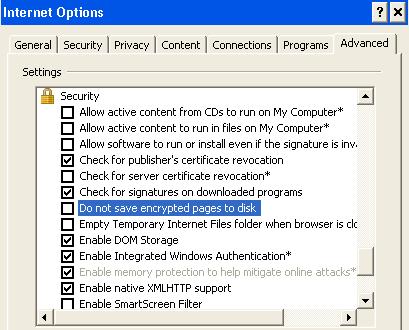
As the Transmission Module is based on Java Web Start, it is mandatory that the JNLP files are properly supported by Java.
This association is automatically set up when installing Java, but sometimes a specific Internet Explorer option may prevent it to run properly.
Solution:
1. In Internet Explorer, navigate to Tools > Internet Options.
2. Select the Advanced tab.
3. Scroll down to Do not save encrypted pages to disk.
5. Disable the checkbox label Do not save encrypted pages to disk.
6. Click OK and click Apply.
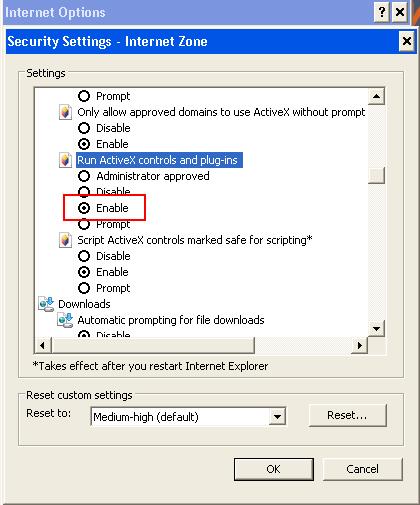
Running ActiveX
The Transmission Module needs the ActiveX controls and plug-ins to be enabled. This association is automatically set up when installing Java, but sometimes a specific Internet Explorer option may prevents it to run properly.
Solution:
1. In Internet Explorer, navigate to Tools > Internet Options.
2. On the Security tab, select a network zone.
3. Click Custom Level.
4. Scroll down to the Run ActiveX controls and plug-ins.
5. Select the checkbox label Run ActiveX controls and plug-ins.
6. Click OK and click Apply.
Error message: Waiting files to transmit...
This message might occur when there is a connection problem between your proxy and the Transmission Module.
Close the Transmission Module :
Activate the Java Console, try to resend your files and check the logs.
If an error 407 appears, it means that the Transmission Module is not able to authenticate on your proxy (407 Proxy Authentication Required)
As a consequence all communications with e-file are blocked.
In that case the solutions to resolve this problem are the following :
By-pass the proxy for the communication with:
www.e-file.lu/WSEfileFlex
www.e-file.lu/WSEfile
www.e-file.lu/ECH
Error message: The process takes too much time
The error message occurs when the Transmission Module could not be launched in time.
Please ensure that:
(-) Your system (proxy, antivirus,...) allows .jar and .jnlp files to be downloaded
(-) The ports 80 (HTTP) and 443 (HTTPS) are enabled
(-) your proxy by-passes the communication with:
www.e-file.lu/WSEfileFlex
www.e-file.lu/WSEfile
www.e-file.lu/ECH
Teamviewer
Click the link below in order to get remote assistance:
(-) Get remote assistance Windows compatible executable
(-) Get remote assistance MAC compatible executable
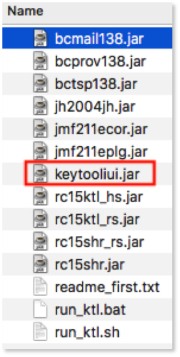
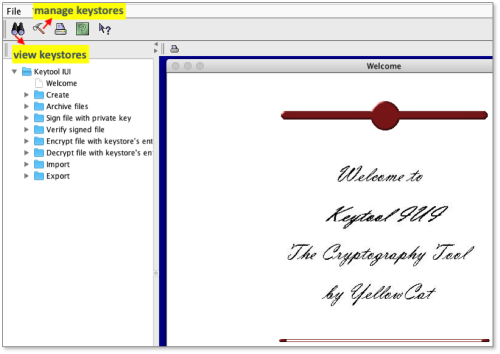
KeyTool
KeyTool is an independent Java software which can be downloaded by clicking the link below:
To open it, double click on keytooliui.jar
Why to merge two keystores
While renewing a Luxtrust certificate, the Transmission Module sometimes creates a new keystore file instead of amending the existing one. This happens when the existing keystore is not selected during the keys generation. The new keystore then allows all E-file functionnalities. However, documents encrypted with or for one of your old certificates cannot be opened.
This article explains how to merge two keystores.
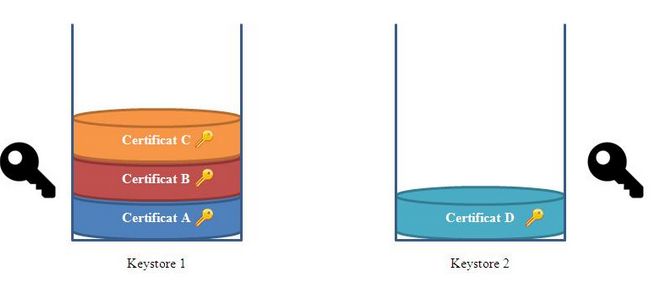
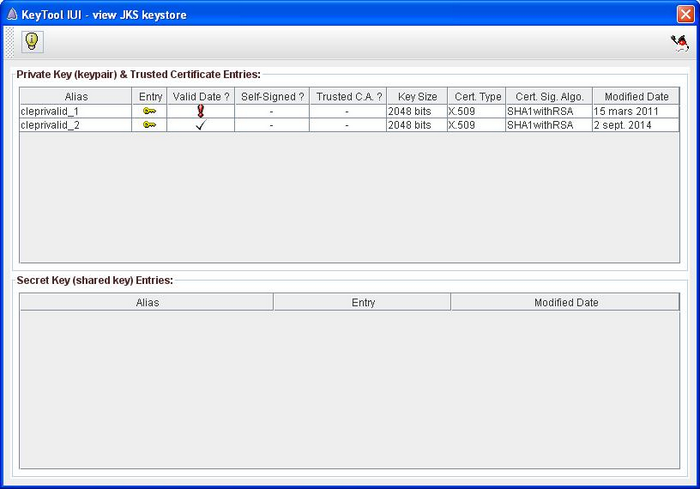
How does a keystore work
Keystore is a Java technology that keeps an history of your certificates like a stack. It is a small file which extension is ".ks" and contains a list of certificates.
Every certificate contains a public key but also a private key which is protected by a password (symbolized ![]() ). The keystore access is protected by a password as well (symbolized
). The keystore access is protected by a password as well (symbolized ![]() ). The private key password and the keystore password must always match, thus
). The private key password and the keystore password must always match, thus ![]() =
= ![]() . For this reason make sure to always use the same password while handling the keystore.
. For this reason make sure to always use the same password while handling the keystore.
During encryption or decryption, the Transmission Module will browse the different keystore's certificates in order to find the associated private key. That's why it's better to have all your company's certificates inside the same keystore.
On the previous sketch, the certificate D has been inserted in a new keystore (keystore 2). For convenience reasons, we prefer putting it in the other keystore (keystore 1) at the top of the pile.
How to merge two keystores
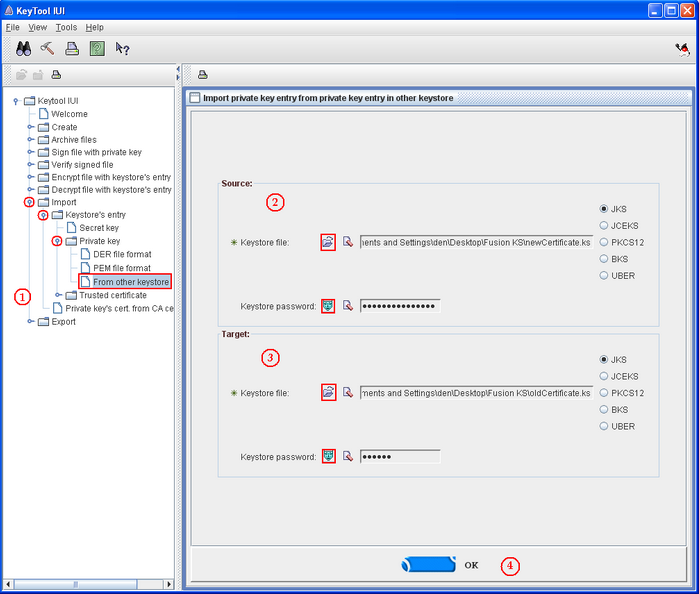
The merging of two keystores is done thanks to an independent Java software called KeyTool which can be downloaded at the following link : [[1]]. To open it, double click on keytooliui.jar.
Follow all the steps to import public and private key from a certificate to another.
- Select "Import private key from other keystore" as shown on the above printscreen (step 1)
- Click on the two icons in the "Source" section in order to select the keystore containing the certificate to import (step 2). The source keystore corresponds to Keystore 2 of the "How does a keystore work" section sketch.
- Do the sane for the target section that selects the keystore on which import the certificate (step 3). The target keystore corresponds to the Keystore 1 of the of the "How does a keystore work" section sketch.
- Click OK (step 4)
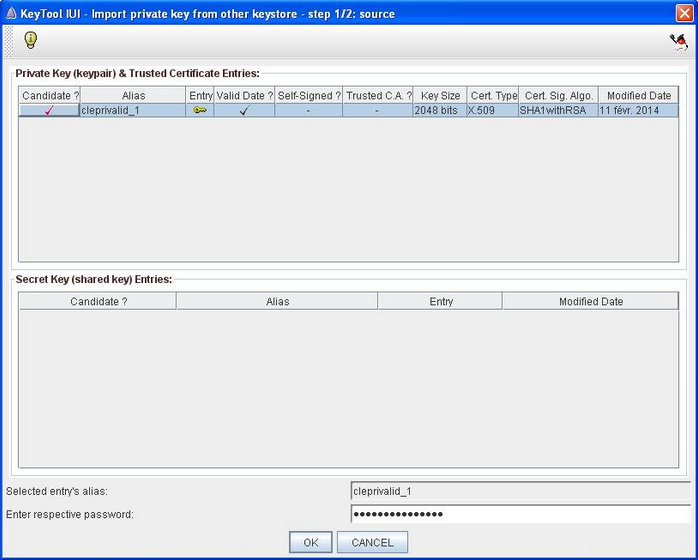
- Select the certificate (that contains the private key) of the source keystore that you desire to import, input its password in the specific field at the bottom of the window.
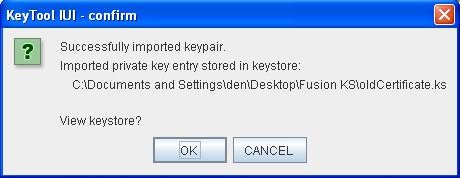
Click OK
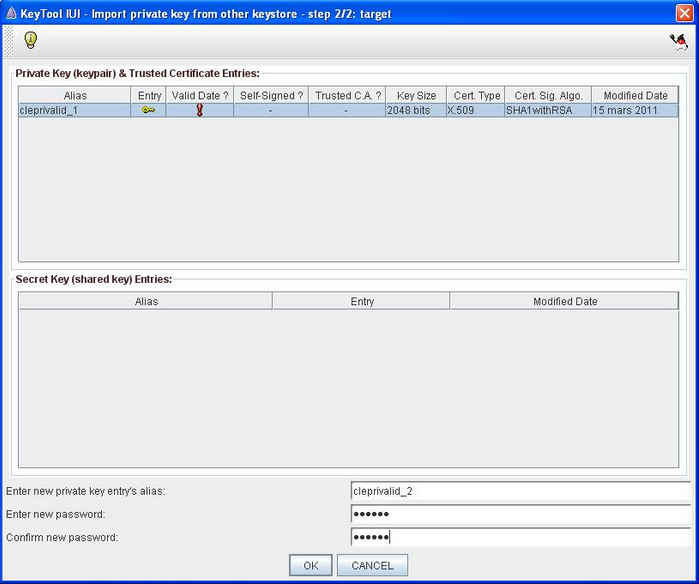
Input the name of the new private key that will be generated in the target keystore. The naming convention is :
cleprivalid_ + incremented number.
As an example, if the target keystore contains already 4 certificates, it has the following entries :
- cleprivalid_1
- cleprivalid_2
- cleprivalid_3
- cleprivalid_4
The new key name will be cleprivalid_5.
- Input the password that will be associated to the new key. Warning : it must be the same as the other private key's password of the target keystore (the one of the keystore). Confirm password.
- Click Ok
The following window appears to indicate the success of the import. When clicking Ok you will see the target keystore content that should contain the imported certificate.